End Point Security
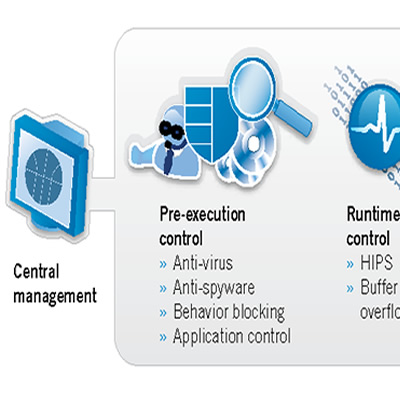
Cyber Security Africa through our partners provides intrusion prevention systems that identify possible intrusions to your network and stops them, preventing further risk. Features include: blocks dangerous communications can protect against dangerous peer-to-peer and instant messaging communications; - easy-to-use browser-based interface. - inspect incoming emails for a variety of threats, including email viruses,spam, spyware, and phishing attacks.
Intrusion Prevention Systems
Cyber Security Africa through our partners provides intrusion prevention systems that identify possible intrusions to your network and stops them, preventing further risk. Features of the IPS include: blocks dangerous communications can protect against dangerous peer-to-peer and instant messaging communications easy-to-use browser-based interface. inspect incoming emails for a variety of threats, including email viruses,spam, spyware, and phishing attacks.
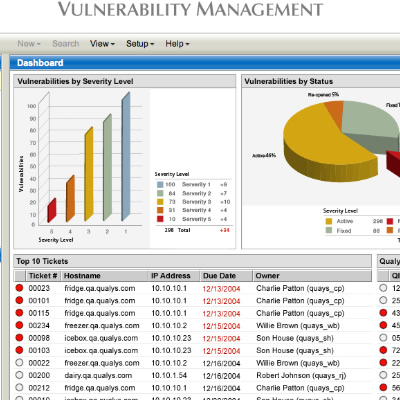
Vulnerability Management
Network security breaches are most commonly caused by missing network patches.Patch management is vital to your business. Cyber Security Africa through our partners provide appliances that scans and detects network vulnerabilities before they are exposed, reducing the time required to patch machines on your network.
Full disk encryption
We ensure data privacy by encrypting data stored on your endpoints especially laptops,Mobile Phones, IPads, tablets, DVDs, and USB drives, which can easily be lost or stolen. Endpoint Encryption provides the data security you need with full disk encryption, folder and file encryption, and removable media encryption.
Source Code Analysis
Static code analysis delivers security and the requirement of incorporating security into the software development lifecycle . It is the only proven method to cover the entire code base and identify all the vulnerable patterns using static code analysis tools. In static code analysis the entire code base is abstracted and all code properties and code flows are exposed. We goe beyond all other static code analysis tools and store all these code...
Network Access Control Systems
NAC is ideal for corporations and agencies where the user environment can be rigidly controlled. It is also called network admission control, a method of bolstering the security of a proprietary network by restricting the availability of network resources to endpoint devices that comply with a defined security policy.
SIEM Management
SIEM consolidates log source event data from thousands of devices endpoints and applications distributed throughout a network. It performs immediate normalization and correlation activities on raw data to distinguish real threats from false positives. As an option, this software supplies a list of potentially malicious IP addresses including malware hosts, spam sources and other threats.
Computer Forensics Equipment
Designed for Field Application, this Computer Forensic Portable Lab is used by Law Enforcement Agencies as well as Corporate Security to acquire data and analyze data in the field. It can be used to image hard drives of any kind as well as capturing data from other media and unopened computers, and supports different copy formats and hashing methods.
Mobile Forensics Equipment
Cyber Security Africa Mobile Forensic team are able to extract key evidence from cellular phones, Smartphones, PDA’s, GPS units and other mobile devices. Using specialized software and equipment designed specifically for advanced cell phone forensics, We are able to extract active and deleted data from many cell phones on the market today.